Looking for the quickest route to encryption in Thunderbird? You might skip to Section 4. The rest of it covers generating, managing and using GPG keypairs in Linux.
This tutorial aims at showcasing how easy it is to fully encrypt emails at a military-grade security level, provided the secret encryption keys do not fall into the hands of any eavesdropper.
The PGP encryption standard, among other things, allows for asymmetric cryptography, the details of which I won't be covering here. The basic idea is that each person taking part in the conversation has two keys: a public key that can be freely distributed to anyone and a private (also named secret) key which should never see the sun or transit through the internet.
If Alice wants to email Bob, she will use Bob's public key to encrypt the content of the email and then she can send it over a network (that could be listened to by an evil eavesdropper) to Bob, which will then in turn decode the email using his private key. The private key is the only computationally feasible way of decoding the message (at least with present day computing, assuming that the key pair is long enough).
If you are a Linux user, you can generate a pair of public-private keys by running the following command:
gpg --full-gen-key The gpg program implements this PGP protocol in Linux. Once you execute the command,
you will be prompted with which kind of key you want.
The default encryption scheme is RSA, the first option. You will now select the keysize. I recommend the maximum allowed
which is 4096. You can set an expiry date for your key, which I usually don't set. This is insecure if you lose it,
but I'm very careful about where I place my private key.
After that you will be asked for a real name and an email address. Unless you publish your public key, this is of almost no consequence at all, you are not signing up to anything anywhere, but if you want to use this key for email encryption, you should put your email adress, as it is the basic identifier that the program gpg uses. The PGP standard allows for encrypting email as well as signing them so if you want to be serious about this use some identifiable name or alias. In this example I will be creating a GPG keypair for myself, Jesus, for use with my email adress jesus@jesusaguado.xyz.
After that, you will be required to enter a passphrase. This passphrase, which you shouldn't forget or lose is used to lock your private key. Even if your private key will be sitting within your computer, everytime you use it you will be required to enter the passphrase (although there is some time after entering the passphrase in which it stays unlocked, for example if you want to decrypt several emails). You can also enter no passphrase at all, but then anyone with physical access to your computer will be able to decrypt anything encrypted with your public key.
Once that process is over, you can check that you have generated a public and a private key with corresponding
commands gpg --list-public-keys and gpg --list-secret-keys.
If you just want to start encrypting mail, you may want to skip this section, although I consider it enlightening to see how to manually do things yourself.
Now that you have a keypair you can already start encrypting any kind of files you like. Let us say that you have
some file personal_diary.txt that you would like encrypted. Then you can run,
on the same directory where the file is stored,
gpg --encrypt --recipient jesus@jesusaguado.xyz personal_diary.txt Now you will notice the appeareance on the current directory of the file personal_diary.txt.gpg.
Bear in mind that asymmetric algorithms are meant to be for exchanging information, so it makes sense that we consider
Jesus (us) to be the recipient of the message. Only Jesus's secret key can decrypt the .gpg file. Let's prove it!
Delete the original plaintext file rm personal_diary.txt and decrypt the cyphertext with
gpg --decrypt personal_diary.txt.gpg > decrypted_diary.txtThe gpg program detects that this file was meant for Jesus to receive, and it knows that we own the secret key
associated with jesus@jesusaguado.xyz, so it uses it. Note the piping > for writing the output of the gpg
program to the file where we store the decrypted text, decrypted_diary.txt.
This section is about how you can generate or import cryptographic keys into your Thunderbird mail client. This works for Linux, Mac and Windows users, just that Linux users will be able to manually generate and use their GPG keys as explained above.
So let us set up our mail client to encrypt and decrypt mail with our newly acquired cryptographic skills. At this point, I am assuming that you use some sort of email client such as Thunderbird. I sincerely hope you do not access your mail through some webclient. I don't know if some webclients support PGP encryption, but I hope they don't (would you trust giving your private key to Gmail to keep it for you?).
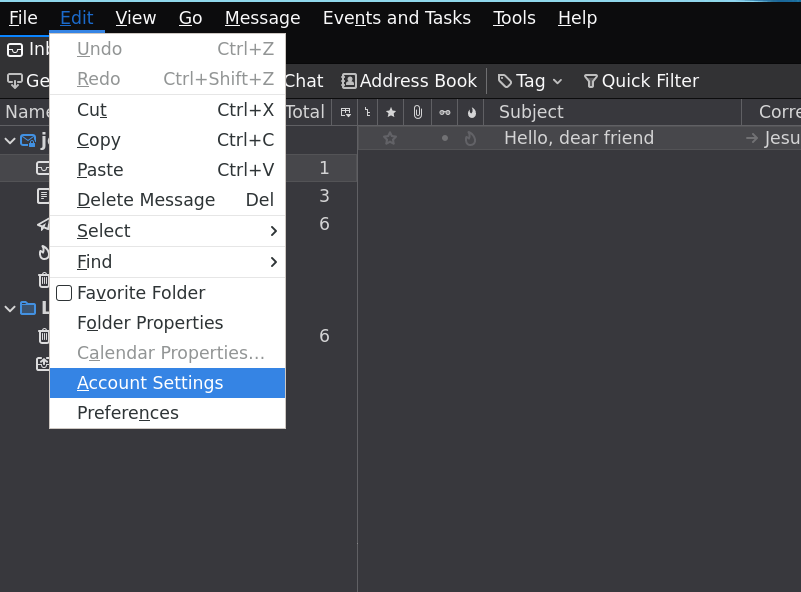
Now, under Thunderbird you can actually generate or import an existing a keypair. You should look at the configuration options, more concretely Account settings. Under your personal account settings (we assume the account is jesus@jesusaguado.xyz) you should see the End-To-End Encryption submenu, whithin which you can see a section called OpenPGP. It will tell you that Thunderbird doesn't have a personal OpenPGP key for jesus@jesusaguado.xyz.

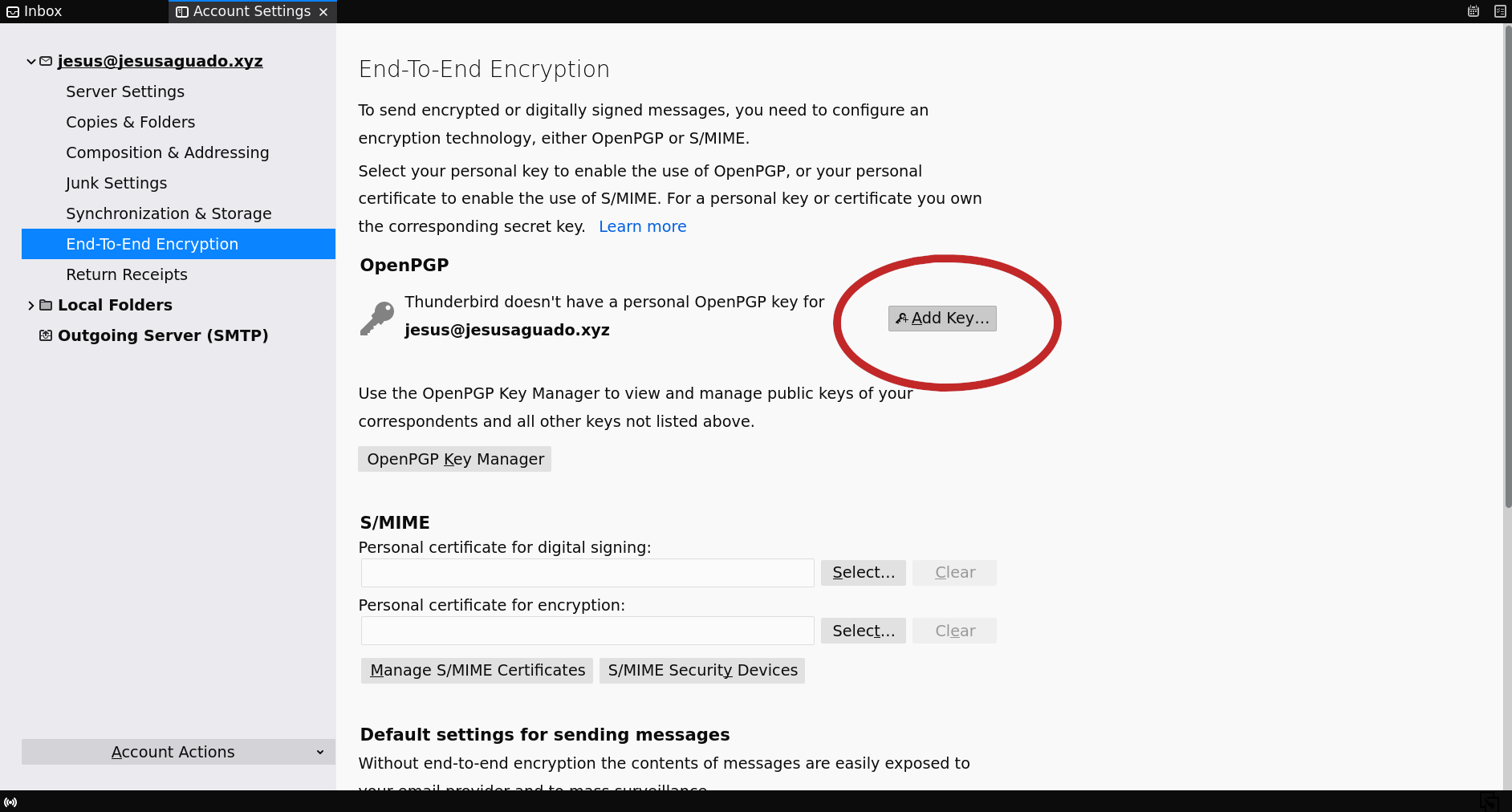 Now you can either:
Now you can either:
gpg --export-secret-key --armor jesus@jesusaguado.xyz > jesus_secretkey.ascNow that you have set up your secret key (and with it, the public key, actually) you can start encrypting mail. Imagine I want to send an encrypted mail to my friend John Doe. To do so, I need to have his public key. I can import it from an ASCII file like the one I generated above, after having kindly asked him to give it to me. To import it, you want to open the OpenPGP Key Manager (you can find it in the tool bar, under "Tools").
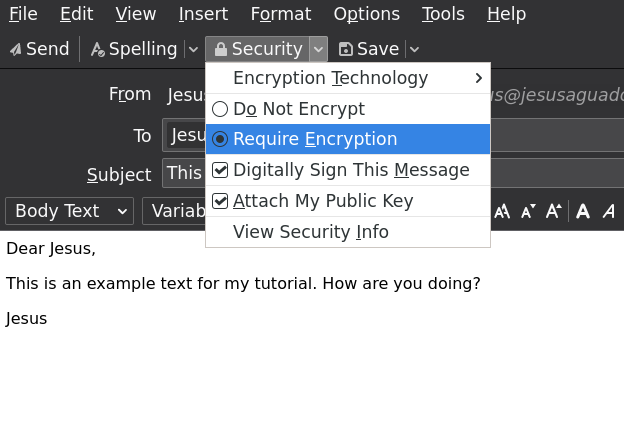
Once that is done, I can compose and encrypt an email (in this example I will be sending it to myself instead). I just need to tell Thunderbird to please encrypt it in the drop-down menu Security, and selecting Require Encryption. Thunderbird will not allow you to do this unless you have the recipient's public key. By default Thunderbird will also sign the message and attach your own public key, which is useful for the first communication.
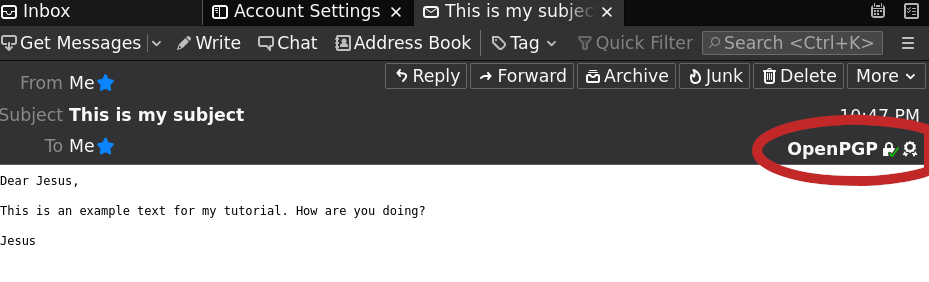
If you are emulating me and sending an encrypted email to yourself, you can check that the email you receive is encrypted (and signed) by looking at the top right-corner (see image below). Clicking on the button will show you additional information.
 Now this might seem a little tedious, and I've got great news for you. There are email clients that are way more customizable than
Thunderbird. Personally, I use Neomutt, and encrypting is as easy as pressing the key "p" after composing the email body.
Now this might seem a little tedious, and I've got great news for you. There are email clients that are way more customizable than
Thunderbird. Personally, I use Neomutt, and encrypting is as easy as pressing the key "p" after composing the email body.
For basic file encryption you can check
this guide, but for more in-depth knowledge concerning subkeys and revocation certificates, you might want to check out
Alex Cabal's page. You should definitely check the man page,
of course man gpg.
Have you seen something inaccurate here? You can contact me at jesus@jesusaguado.xyz if you have seen an error or something that is straight up wrong. My public key can be found here if you want to test and encrypt your mail to me!